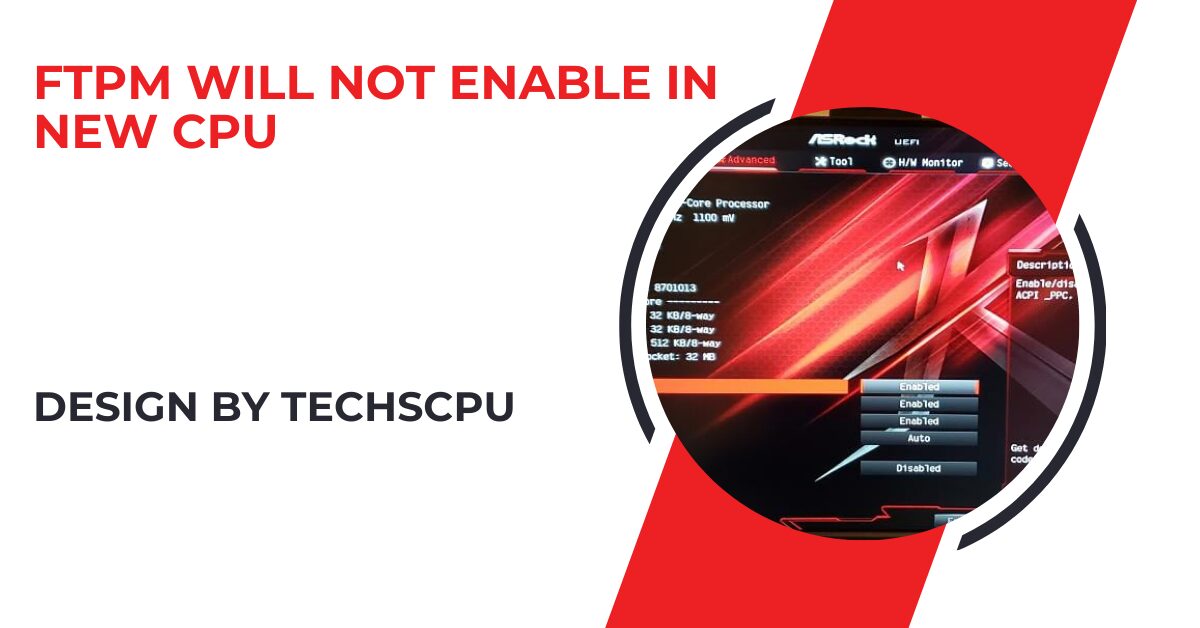
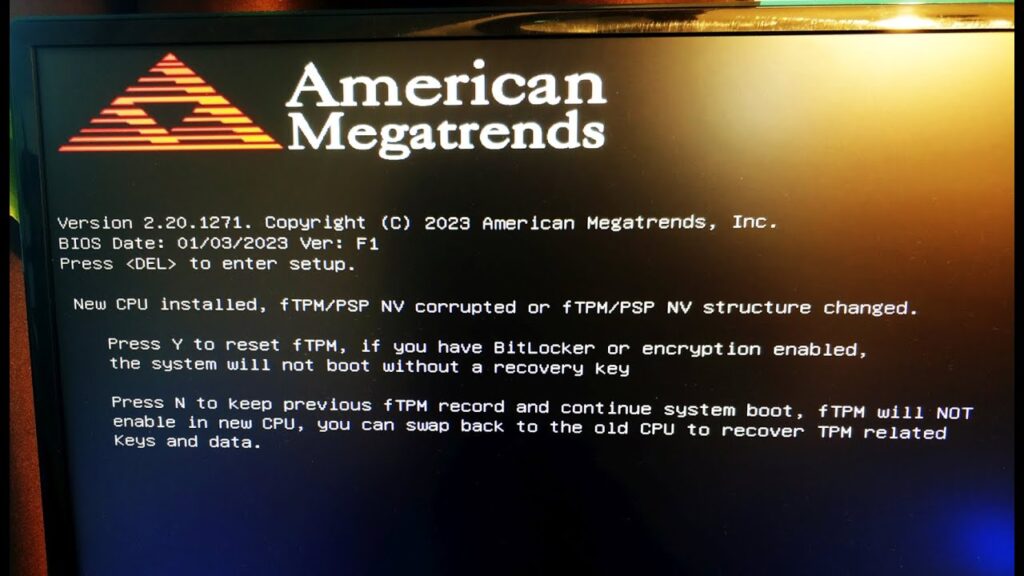
FTPM not enabling in new CPUs poses significant security risks and performance implications due to compatibility issues and configuration complexities.
Introduction:
In the realm of technological advancements, the issue of FTPM (Firmware Trusted Platform Module) failing to enable in new CPUs has emerged as a critical concern. This comprehensive article explores the intricacies of this problem, delving into its implications and offering insights into potential resolutions.
What is FTPM:
FTPM, also known as Firmware Trusted Platform Module, is a pivotal component integrated into modern CPUs to bolster security. It provides a secure enclave for critical cryptographic operations, key storage, and safeguarding sensitive data against unauthorized access.
The Evolution of CPUs and Security Standards:
As CPUs evolve to meet escalating demands for performance and efficiency, security standards such as FTPM have become integral. However, recent developments reveal that certain new CPU models encounter challenges when attempting to enable FTPM.
Reasons Behind FTPM Not Enabling:
Several factors contribute to FTPM not enabling on new CPUs:
- Hardware Compatibility Issues: New CPU architectures may lack full support for FTPM integration, leading to functionality issues.
- Firmware and BIOS Updates: Incompatibilities between firmware versions and CPU models can hinder FTPM activation.
- Configuration Complexity: Challenges in configuring FTPM settings during system setup or upgrades may prevent its proper functioning.
Impact on Security and Performance:
The inability to activate FTPM on new CPUs carries significant ramifications:
- Security Vulnerabilities: Without FTPM, systems may be more vulnerable to attacks targeting cryptographic operations and sensitive data.
- Compliance Challenges: Industries reliant on stringent security protocols may face compliance hurdles if FTPM functionality is compromised.
- Performance Implications: FTPM enhances system performance by offloading cryptographic tasks. Its absence could potentially impact overall system efficiency and responsiveness.
Also Read: Amd Bulldozer Cpu List – A Comprehensive Guide!
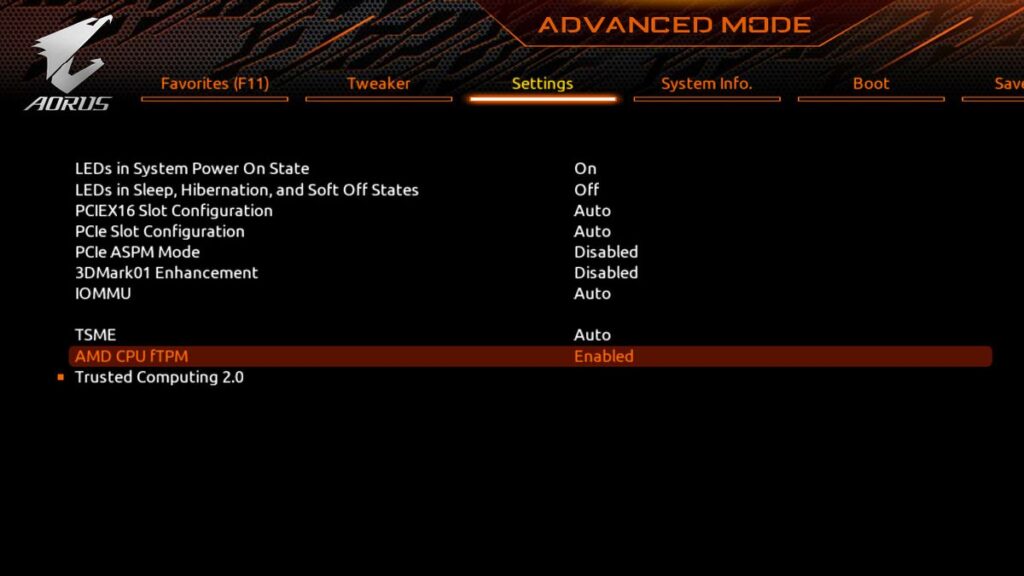
Resolving FTPM Issues: Steps and Considerations
Effectively addressing FTPM issues necessitates a systematic approach:
- Firmware Updates: Ensuring that BIOS and firmware updates are compatible and up-to-date is crucial for enabling FTPM functionality.
- Hardware Compatibility Checks: Conducting thorough assessments to verify that new CPUs meet FTPM specifications and requirements.
- Technical Support and Guidance: Seeking assistance from hardware manufacturers or IT professionals can aid in troubleshooting and resolving FTPM-related issues effectively.
Future Outlook and Developments:
Looking ahead, the trajectory of CPU technology and firmware advancements holds promise for mitigating FTPM-related challenges. Ongoing industry collaborations and research endeavors aim to enhance compatibility and fortify security measures across future CPU releases.
Technological Advancements and FTPM Integration:
Advancements in CPU technology and firmware updates drive FTPM integration forward:
- Advanced Encryption Techniques: Implementing stronger encryption algorithms to enhance data security.
- Hardware Security Enhancements: Developing integrated security features to fortify system defenses against evolving threats.
- Cloud Computing and FTPM: Ensuring secure cloud-based services through robust FTPM integration in data centers and virtual environments.
The Role of FTPM in IoT Devices:
Integrating FTPM into IoT (Internet of Things) devices enhances device security and data integrity:
- Smart Home Applications: Securing connected devices and ensuring privacy in home automation systems.
- Industrial IoT: Protecting critical infrastructure and industrial control systems from cyber threats.
- Automotive Industry: Safeguarding vehicle-to-vehicle communications and connected car technologies.
Challenges in Securing Legacy Systems with FTPM:
Integrating FTPM into legacy systems poses unique challenges and considerations:
- Compatibility Issues: Ensuring backward compatibility with older hardware and software configurations.
- System Performance: Balancing security enhancements with legacy system performance requirements.
- Cost and Resource Allocation: Investing in upgrades and retrofits to incorporate FTPM without disrupting legacy operations.
FTPM and Cloud Computing Security:
FTPM integration in cloud computing environments enhances data security and compliance:
- Virtual Machine Security: Protecting virtualized environments and ensuring data confidentiality.
- Data Integrity and Auditing: Implementing robust FTPM solutions for data integrity checks and audit trails.
- Multi-Cloud Deployments: Securing data across multiple cloud platforms through unified FTPM solutions and standards.
Emerging Trends in FTPM and AI Integration:
Exploring the intersection of FTPM and AI (Artificial Intelligence) technologies:
- AI Model Security: Securing AI model training and inference processes with FTPM-enabled CPUs.
- Privacy-Preserving AI: Implementing FTPM for preserving user privacy and data confidentiality in AI applications.
- Edge Computing and FTPM: Enhancing edge device security and data protection in AI-driven IoT deployments.
FTPM in Blockchain Technology:
Integrating FTPM in blockchain networks enhances transaction security and data integrity:
- Cryptocurrency Transactions: Securing blockchain transactions and wallets against hacking and fraud.
- Decentralized Applications (DApps): Protecting user data and application integrity in decentralized computing environments.
- Smart Contract Security: Ensuring secure execution and validation of smart contracts through FTPM-enabled blockchain nodes.
Also Read: E5 V4 Cpu List – Features, Specs, and Applications!
FTPM and Data Privacy Regulations:
Complying with global data privacy regulations through robust FTPM implementation:
- GDPR Compliance: Safeguarding personal data and ensuring GDPR compliance with FTPM-enabled data processing systems.
- HIPAA Compliance: Protecting patient health information (PHI) and ensuring HIPAA compliance in healthcare IT infrastructures.
- PCI DSS Compliance: Securing payment card data and meeting PCI DSS requirements with FTPM-integrated payment processing systems.
FAQs:
1. What is FTPM?
FTPM stands for Firmware Trusted Platform Module. It’s a crucial component in modern CPUs that enhances security by providing a secure environment for cryptographic operations and key storage.
2. Why is FTPM not enabling in new CPUs?
FTPM may not enable due to hardware compatibility issues, firmware or BIOS update conflicts, and challenges in configuring FTPM settings during system setup.
3. What are the implications of FTPM not enabling?
Without FTPM, systems may be more vulnerable to security breaches targeting sensitive data. It can also affect compliance with industry security standards and impact overall system performance.
4. How can FTPM issues be resolved?
Resolving FTPM issues involves ensuring compatible firmware updates, conducting hardware compatibility checks, and seeking technical support from manufacturers or IT professionals.
5. What is the future outlook for FTPM integration in CPUs?
Ongoing advancements in CPU technology and collaborative industry efforts aim to address FTPM integration challenges, enhancing compatibility and security measures in future CPU releases.
Conclusion:
In conclusion, while encountering FTPM issues in new CPUs presents complexities, proactive measures and a thorough understanding of underlying causes are essential for mitigating risks and upholding robust security protocols. Staying abreast of updates and advancements in CPU technology will be pivotal in leveraging enhanced security features effectively.